Home
Recommended
Other Links
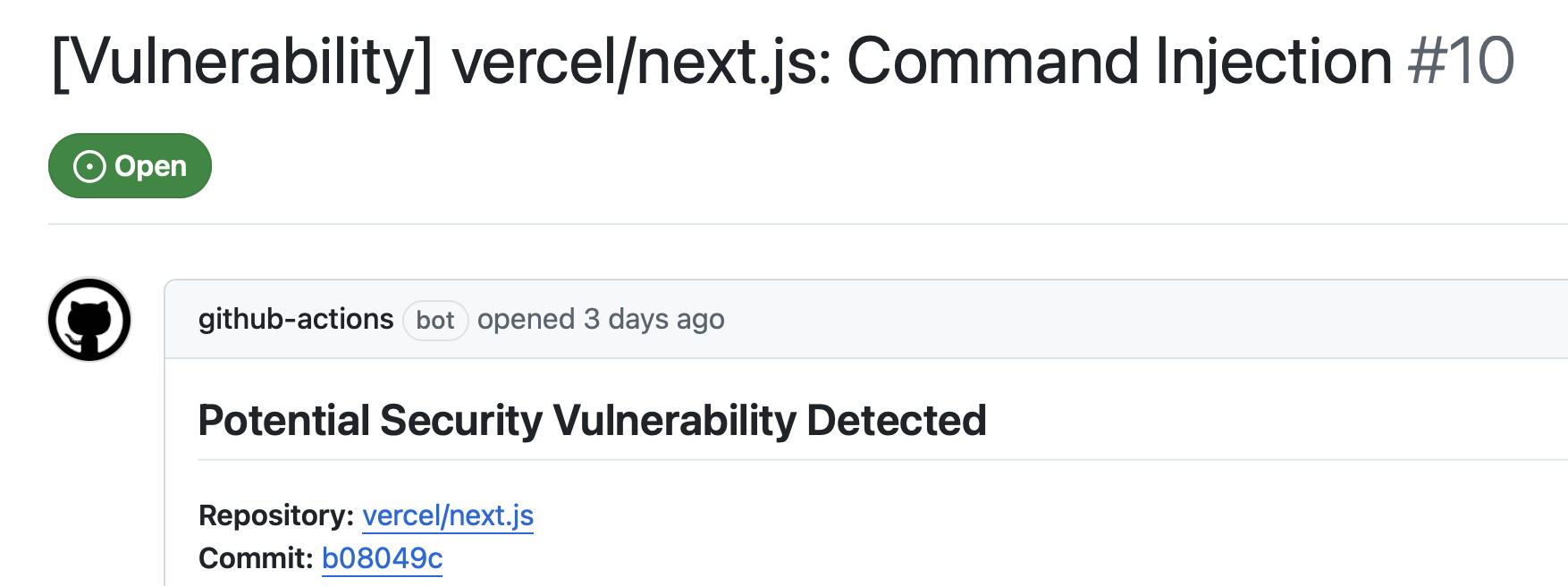
GitHub Security Lab Taskflow Agent is very effective at finding Auth Bypasses, IDORs, Token Leaks, and other high-impact vulnerabilities.
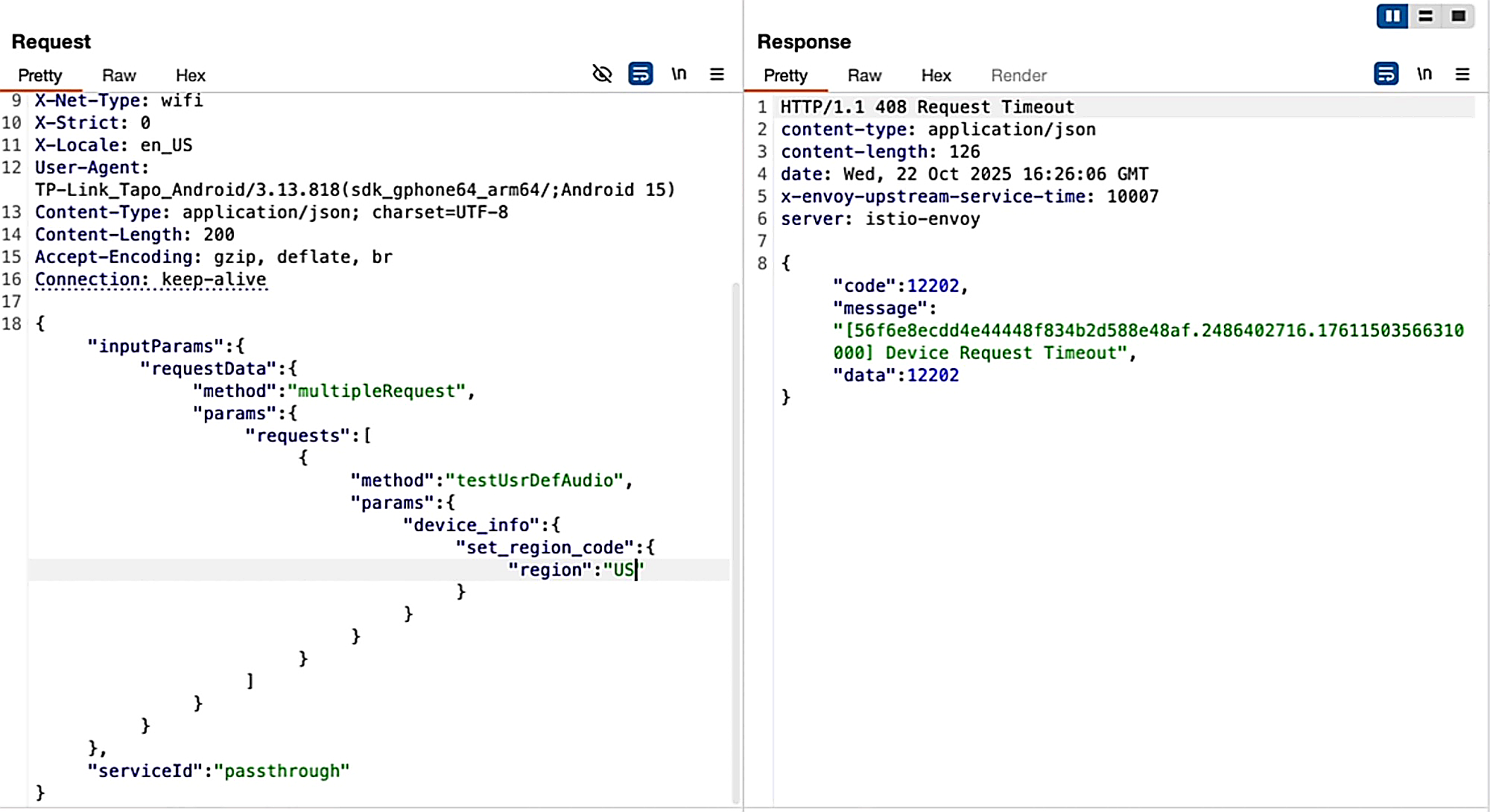
I discovered a remote code execution vulnerability on the Tapo C260 after a fun journey of reverse-engineering and understanding its interactions with TP-Link Cloud.
# The MCP AuthN/Z Nightmare
05 Mar 2026 - Posted by Francesco Lacerenza
This article shares our perspective on the current state of authentication and authorization in enterprise-ready, remote MCP server deployments.
Before diving into that discussion, we’ll first outline the most common...
When a phone starts “taking action” on its own, it’s no longer just answering questions like how to get a cheaper takeout—it can actually open apps, compare prices, and place orders. Control shifts from the user’s fingers to an intelligent agent capable of seeing the screen, planning, and executing tasks.
Launched at the end of 2025, the Doubao Phone Assistant (hereafter Doubao Assistant) was the first to hand over the phone’s full operational chain to an AI agent. It uses a large language model as the central decision-making unit, combined with GUI Agent technology, to understand user intentions, break down tasks, plan paths, and execute complex cross-app and cross-scenario operations with system-level capabilities.
Key Findings Introduction As highlighted in the Cyber Security Report 2026, cyber operations have increasingly become an additional tool in interstate conflicts, used both to support military operations and to enable ongoing battle damage assessment (BDA). During the 12-day conflict between Israel and Iran in June 2025, the compromise of cameras was likely used to support […]
Key Findings Introduction In recent months, Check Point Research (CPR) has been tracking a sophisticated, Chinese-aligned threat group whose activity demonstrates operational correlation with campaigns previously associated with APT41. We have designated this activity cluster as Silver Dragon. This group actively targets organizations in Southeast Asia and Europe, with a particular focus on government entities. […]
On today’s ‘good news disguised as other things’ segment, we’re turning our gaze to CVE-2026-21902 - a recently disclosed “Incorrect Permission Assignment for Critical Resource” vulnerability affecting Juniper’s Junos OS Evolved platform. This vulnerability affects only Juniper’s PTX Series of devices, apparently.
Why? Who cares knows.
Throughout this post, we will be diving into the deepest, most complex vulnerability we have ever seen. Remote Code Execution as a Service (soon to be disrupted
CVE-2026-22891
A heap-based buffer overflow vulnerability exists in the Intan CLP parsing functionality of The Biosig Project libbiosig 3.9.2 and Master Branch (db9a9a63). A specially crafted Intan CLP file can lead to arbitrary code execution. An attacker can provide a malicious file to trigger...
CVE-2026-20777
A heap-based buffer overflow vulnerability exists in the Nicolet WFT parsing functionality of The Biosig Project libbiosig 3.9.2 and Master Branch (db9a9a63). A specially crafted .wft file can lead to arbitrary code execution. An attacker can provide a malicious file to trigger this...
CVE-2025-64736
An out-of-bounds read vulnerability exists in the ABF parsing functionality of The Biosig Project libbiosig 3.9.2 and Master Branch (5462afb0). A specially crafted .abf file can lead to an information leak. An attacker can provide a malicious file to trigger this vulnerability.
The...
Security audit of shift scheduling and workforce management apps finds flaws that expose Plaid banking tokens, allow fake messages under the employer's brand, and let attackers silently delete shift notifications.
Oversecured identifies hardcoded cloud credentials and a cross-site scripting flaw in popular AI companion apps, exposing backend infrastructure and allowing code injection into private conversations.
mitmproxy for fun and profit: Interception and Analysis of Application
The MDSec red team are regularly performing research to identify privilege escalation vectors in Windows and macOS for use during red team engagements. Where the indicators in exploiting the EoP...
It’s been a while, but we’re back - in time for story time.
Gather round, strap in, and prepare for another depressing journey of “all we wanted to do was reproduce an N-day, and here we are with 0-days”.
Today, friends, we’re looking at SolarWinds Web Help Desk, which has seen its fair share of in-the-wild exploitation and while purporting to be a help desk solution - has had far more attention for its ability to provide RCE opportunities, with a confidence-inspiring amount of “oh it’s basica
By Aviv Donenfeld and Oded Vanunu Executive Summary Check Point Research has discovered critical vulnerabilities in Anthropic’s Claude Code that allow attackers to achieve remote code execution and steal API credentials through malicious project configurations. The vulnerabilities exploit various configuration mechanisms including Hooks, Model Context Protocol (MCP) servers, and environment variables -executing arbitrary shell commands […]
2025 winter challenge writeup
It’s been a while since I last dug into a Patch Tuesday release. With an extraordinarily high number of 177 CVEs, including 6 that were either already public or exploited in the wild, the October 2025 one seemed like a good opportunity to get back at it. The one I ended up investigating in depth was CVE-2025-59201, an elevation of privilege in the “Network Connection Status Indicator”.
Introduction Check Point Research (CPR) continuously tracks threats, following the clues that lead to major players and incidents in the threat landscape. Whether it’s high-end financially-motivated campaigns or state-sponsored activity, our focus is to figure out what the threat is, report our findings to the relevant parties, and make sure Check Point customers stay protected. […]
In this excerpt of a TrendAI Research Services vulnerability report, Nikolai Skliarenko and Yazhi Wang of the TrendAI Research team detail a recently patched command injection vulnerability in the Windows Notepad application. This bug was originally discovered by Cristian Papa and Alasdair Gorniak
A Talos researcher used targeted emulation of the Socomec DIRIS M-70 gateway’s Modbus thread to uncover six patched vulnerabilities, showcasing efficient tools and methods for IoT security testing.
CVE-2025-61982
An arbitrary code execution vulnerability exists in the Code Stream directive functionality of OpenCFD OpenFOAM 2506. A specially crafted OpenFOAM simulation file can lead to arbitrary code execution. An attacker can provide a malicious file to trigger this vulnerability.
The...
Key Points Introduction AI is rapidly becoming embedded in day-to-day enterprise workflows, inside browsers, collaboration suites, and developer tooling. As a result, AI service domains increasingly blend into normal corporate traffic, often allowed by default and rarely treated as sensitive egress. Threat actors are already capitalizing on this shift. Across the malware ecosystem, AI is […]
# Building a Secure Electron Auto-Updater
16 Feb 2026 - Posted by Michael Pastor
## Introduction
In cooperation with the Polytechnic University of Valencia and Doyensec, I spent over six months during my internship in a research that combines theoretical foundations in code signing and secure...
"There is a lot of talk about Skills recently, both in terms of capabilities and security concerns. However, so far I haven\u0026rsquo;t seen anyone bring up hidden …"
Oversecured has identified vulnerabilities in several popular mental health apps with tens of millions of downloads. The flaws could turn these apps into unintended data sources for surveillance, including personal conversations with AI therapists.
It’s no longer just about reverse-engineering n-days. You can detect vulnerabilities in open-source repositories before a CVE is published - or even if they’re never published. Here’s how I built an LLM workflow to detect “negative-days” and “never-days”.
In this excerpt of a TrendAI Research Services vulnerability report, Jonathan Lein and Simon Humbert of the TrendAI Research team detail a recently patched command injection vulnerability in the Arista NG Firewall. This bug was originally discovered by Gereon Huppertz and reported through the Tren
Welcome to the Top 10 Web Hacking Techniques of 2025, the 19th edition of our annual community-powered effort to identify the most innovative must-read web security research published in the last year
"Last week I saw this paper from OpenAI called \u0026ldquo;Preventing URL-Based Data Exfiltration in Language-Model Agents\u0026rdquo;, which goes into detail on new …"
TL;DR In December 2025, Cisco published https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sma-attack-N9bf4 addressing CVE-2025-20393, a critical vulnerability (CVSS 10.0) affecting Cisco Secure Email Gateway and Secure Email and Web Manager. The advisory was notably sparse on technical details, describing only “Improper Input Validation” (CWE-20).
We decided to dig deeper. Through reverse engineering and code analysis of AsyncOS 15.5.3, we uncovered the root cause: a single-byte integer overflow in the EUQ RPC protocol that bypasses authentication and chains into Python pickle deserialization — achieving unauthenticated remote code execution with a single HTTP request.
A friend of mine, namely Antide "xarkes" Petit, came up with a pretty good rule of thumb that I think should be elevated into a law, Antide's Law:
> If it's unclear what a cyber-security company is doing, what they're doing is pretty clear.
For example, take a look at Offensive Con 2025 and 2024...
Key Points Introduction Check Point Research has identified several campaigns targeting multiple countries in the Southeast Asian region. These related activities have been collectively categorized under the codename “Amaranth-Dragon”. The campaigns demonstrate a clear focus on government entities across the region, suggesting a motivated threat actor with a strong interest in geopolitical intelligence. The campaigns […]
Discover how Mercari, Japan's largest marketplace app, transformed their mobile security program with Oversecured, uncovering critical vulnerabilities missed by previous tools and achieving reliable automated scanning at scale.
# Auditing Outline. Firsthand lessons from comparing manual testing and AI security platforms
03 Feb 2026 - Posted by Luca Carettoni
In July 2025, we performed a brief audit of Outline - an OSS wiki similar in many ways to Notion. This activity was meant to evaluate the overall posture of the...
The Google Groups Ticket Trick vector is alive and well, allowing me to briefly verify an openssl.org email address. Also, vibe-coding security tools is easier than ever.
Beyond ACLs: Mapping Windows Privilege Escalation Paths with
When Ivanti removed the embargoes from CVE-2026-1281 and CVE-2026-1340 - pre-auth Remote Command Execution vulnerabilities in Ivanti’s Endpoint Manager Mobile (EPMM) solution - we sighed with relief.
Clearly, the universe had decided to continue mocking Secure-By-Design signers right on schedule - every January.
Welcome back to another monologue that doubles as some sort of industry-wide counseling session we must all get through together.
As we are always keen to remind everyone, today’s blo
Check Point's flagship report delivers industry leading intelligence shaping the decisions security leaders will make in 2026
[this work was conducted collaboratively by Bryan Alexander and Jordan Whitehead] This post details several vulnerabilities discovered in the popular online game Command & Conquer: Generals. We recently presented some of this work at an information security conference and this post contain
On the clock: Escaping VMware Workstation at Pwn2Own Berlin 2025
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
North Korea-linked threat group KONNI targets countries across APAC, specifically in blockchain sectors, with AI-generated malware
Well, well, well - look what we’re back with.
You may recall that merely two weeks ago, we analyzed CVE-2025-52691 - a pre-auth RCE vulnerability in the SmarterTools SmarterMail email solution with a timeline that is typically reserved for KEV holders.
The plot of that story had everything;
* A government agency
* Vague patch notes (in our opinion)
* Fairly tense forum posts
* Accusations of in-the-wild exploitation
The sort of thing dreams are made of~
Why Are We Here?
Well, as alway
### Summary
It is still possible (albeit with significantly more effort) to upload a specially crafted Wheel file (i.e. zip) to PyPI that when installed with PIP (or another Python zipfile based t...
# Intercepting OkHttp at Runtime With Frida - A Practical Guide
22 Jan 2026 - Posted by Szymon Drosdzol
### Introduction
OkHttp is the defacto standard HTTP client library for the Android ecosystem. It is therefore crucial for a security analyst to be able to dynamically eavesdrop the traffic...
Learn how we are using the newly released GitHub Security Lab Taskflow Agent to triage categories of vulnerabilities in GitHub Actions and JavaScript projects.
VoidLink's framework marks the first evidence of fully AI-designed and built advanced malware, beginning a new era of AI-generated malware
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...